Core Cybersecurity for Applications
Safeguard your systems with effective tools for threat detection, response and reporting
Overview
In today’s ever-evolving digital world, cybersecurity has become increasingly paramount. As our reliance on technology deepens, so does the sophistication of cyber threats. Organizations and individuals alike face a constant barrage of attacks, ranging from phishing scams to ransomware assaults.
Investing in robust cybersecurity measures is not merely an option but a necessity for survival in today’s interconnected world.
Experience a new dimension of cybersecurity excellence with Sirma. Our experts provide traditional monitoring and incident response utilizing best-in-class technologies to detect and prevent cyber threats proactively. Beyond mere protection, we offer comprehensive solutions, ensuring holistic protection for your digital assets. We leverage cutting-edge technology, staying one step ahead of cyber threats. With unmatched expertise, our professionals navigate the complexities of cybersecurity with precision.
Service Description
Why trust us with your Cybersecurity?
Cybersecurity in today’s connected world is a fundamental component of any business. Weak security practices can result in a major service disruption and data breach. When it comes to safeguarding your business and possibly that of your customers from cyber-attack, you want the most effective tools for threat detection, response and reporting at your disposal.
With over 20 years of experience in core C, C++, Java and .NET programming, we at Sirma address your lists of security issues and vulnerability findings and put in place the often missing security components in the existing DevOps processes.
How do we safeguard your systems?
Most of enterprises have done a fairly good job of protecting the network layer and endpoints of the cybersecurity surface; however, the application layer remains especially vulnerable to cybersecurity risks, which means the primary focus of the enterprise’s security plan today must be on applications.
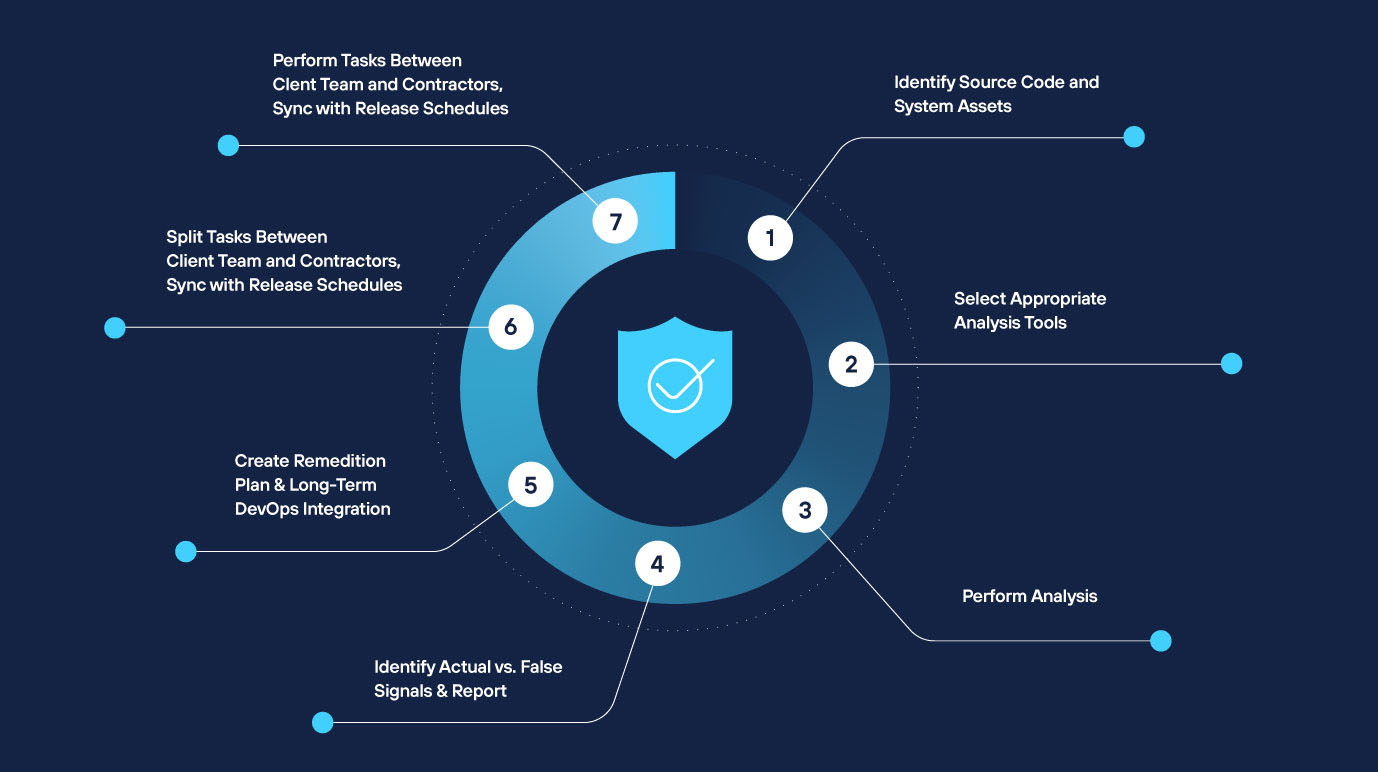
Source-code level security remediation services
Instead of focusing on discovering and reporting vulnerabilities, we at Sirma offer source-code-level security remediation services. We instrument your codebases with automated security vulnerability scanning and fix discovered issues by working in parallel with your software teams so that planned feature releases are not delayed while working on security concerns.
Our leverage is our unique expertise with embedded IoT systems across platforms from NXP, Freescale, Odroid, TI, Ricoh, Konica-Minolta and Fujitsu.
Security Operation Center (SOC) Services
Rely on our top-tier experts for comprehensive Security Operations Center (SOC) services, ensuring unwavering protection for your business.
- Continuous monitoring of network activity
- Vulnerability assessments and patch management
- Incident response and forensics investigation
- Detection and prevention of cyber threats
- Analysis and correlation of security events
Learn more
CISO (Chief Information Security Officer) as a Service
By placing your cybersecurity in the hands of our CISO as a Service, you can be confident that your organization is well-guarded against cyber threats. This assurance enables you to concentrate on your core business activities without the constant concern of potential security risks.
- Risk assessment
- Ongoing security management
- Incident response planning
- Policy development
- Security audit
- Training and education for employees
Penetration Tests
Empower your organization with our penetration testing services, offering invaluable insights to fortify your defences and shield against potential threats.
- Network penetration testing
- Web application testing
- Wireless network testing
- Social engineering testing
Why work with us
Cost-effective and reliable cybersecurity
We heavily rely on security testing which is very important and makes comprehensive cybersecurity for applications simpler and more cost-effective. Our cybersecurity services are specialized in the applications layer and we do source-code level security remediation services.
Sirma’s programmers are cybersecurity professionals and they simply think as an attacker does. We use formal verification methods and like an external auditor PCI certification, we would expect independents to deliver more objectivity.
Protect your IT systems with top cybersecurity solutions.
Transform your business
Sirma offers the most advanced suite of AI applications for complex manufacturing, logistics & consumer products.
Work with us
